
Last year I wrote Tax Season Equals Fraud Season, and this year is no different. On February 3, the IRS issued an urgent alert warning businesses that threat actors are again using the same executive impersonation scam from last year, except in 2017 they have expanded beyond for-profit businesses to non-profit organizations, such as schools, tribal organizations, and non-profits.
The most prevalent type of scam in circulation at the moment is often referred to as Business Email Compromise (BEC) or Business Email Spoofing (BES). Essentially it consists of a cleverly manufactured email designed to look legitimate – often using lookalike domain names to send the email (such as rnarkmonitor.com – notice the double “rn” at the front) – and have the appearance of coming from an executive. The email often asks for internal data that only a high level executive can typically ask for and receive without additional checks and balances.
During Tax Season, the email often targets Human Resources or Payroll managers, and they specifically request employee W-2 files. Threat actors comb LinkedIn and other social media sites to find the information they need to specifically target an individual employee, such as this example:
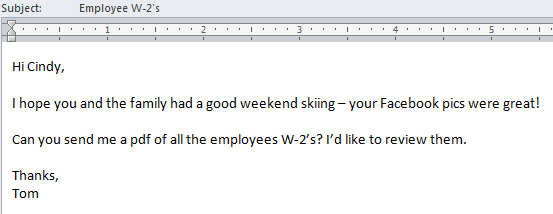
United States Internal Revenue Service (IRS) W-2 Tax Forms are distributed in January every year by organizations to both their employees and the IRS reporting the employee’s annual wages and the amount of taxes withheld from their paycheck over the past year. The form also conveniently includes all pertinent information needed to file a basic tax return – including the employee’s Social Security Number and current address.
“This is one of the most dangerous email phishing scams we’ve seen in a long time. It can result in the large-scale theft of sensitive data that criminals can use to commit various crimes, including filing fraudulent tax returns. We need everyone’s help to turn the tide against this scheme,” said IRS Commissioner John Koskinen.
How to Protect Your Organization
- Employee education, awareness & empowerment are key to fighting these social engineering tactics. Each employee must understand they are the first line of defense and should question out of the norm communications.
- Employees (and all consumers in general) should be suspicious of pressure to take urgent action, or action outside of normal business practices.
- Train team members to hit “forward” instead of “reply” so they are forced to type or select the correct “To:” email address.
- Pre-establish internal checks & balances that prevent one person from being able to send a wire transfer or email sensitive information such as an entire employee roster.
The IRS is recommending organizations report receiving W-2 scams to both the IRS at phishing@irs.gov with the subject line “W2 Scam” and to the FBI’s Internet Crime Complaint Center (IC3).
For individuals whose W-2 forms may have been compromised, the IRS advises reviewing recommended actions by the Federal Trade Commission (FTC) at www.identitytheft.gov or the IRS at www.irs.gov/identitytheft.
Additionally, during tax season often there are other IRS related scams in the form of phone calls demanding payment for a tax return. The IRS will never demand payment over the phone, call you for personal information, or threaten to bring in local law enforcement for non-payment arrest. Do not give out any personal information over the phone when you receive a call of this nature. Call the IRS at 800-829-1040 for help.