
What are the 2018 cybercrime trends?
Well, there are a lot, from cryptocurrency – a new, emerging threat that I feel like we’ll be talking more about as the year goes on – to rising concerns over the Internet of Things attacks. Then there are the tried-and-true attacks: classic phish, smishing and vishing that are still very effective.
For the purpose of this two part series, I will focus on three prevalent trends that are most egregiously targeting our branded customers.
Most commonly detected trends in the first quarter of 2018:
Part 1:
- SSL certs used in phishing
- BEC scams and targeted spearphishing
Part 2:
- One-time use URLs
Additionally, I’ll cover the value of enforcing on the collection point email addresses found in phish kits. Shutting down the collection point email address (where phishing credentials are collected) can disrupt a phisher’s business and make your brand a harder target.
Part 1: SSL certs used in phishing
SSL or TLS certs on a website encrypts the communication between a web server and a browser, allowing communications with the website to remain private and protecting the user’s information. Use of SSL/TLS certs are an industry standard, and are purchased through a certificate authority.
There are 3 basic types of certs:
- The most basic level is a domain validation cert, or DV cert. The validation for a DV cert is simply verifying that the person applying for the cert is associated with the ownership of the domain.
- Organization validation certs, or OV certs, validate that the domain name is associated with the organization.
- Extended validation certs, or EV certs, are the gold standard for ecommerce and financial entities because the certificate authority provides extensive validation prior to issuing these certs.
This all sounds good, right? Except that phishers have figured out how to capitalize on the average consumers misunderstanding of how certs work. Most consumers believe a that a cert (indicated by the s” appended to the http in a web address or the padlock or word “secure” in the address line) means that the site is not only legitimate but totally secure assuming that the data they transmit (like login credentials or payments) are encrypted and protected. They also tend to believe that only legitimate verified organizations can purchase an SSL/TLS cert.
If only that were true! There are a few different certificate authorities that offer short term DV certs; perfect for the phishers to accomplish their purposes. DV certs only verify that an applicant is related to the domain ownership. When a consumer enters credentials or payment criteria in one of these malicious sites the data is encrypted to everyone except the domain owner; unfortunately in this scenario the domain owner is also the phisher.
In a February 2018 report Zscaler reported a 300% increase in phishing attacks; plus 74% of blocked SSL content in the Zscaler cloud were utilizing DV certs.
OpSec detections have indicated at 260% increase in the last 12 months on validated phishing sites utilizing an SSL cert:
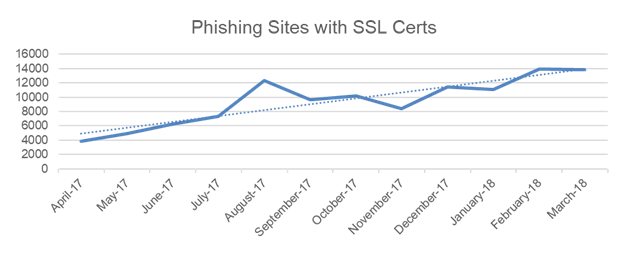
To efficiently detect and mitigate these types of phish the OpSec AntiFraud Security Operation Center started processing an additional detection feed in 2017 focused on the identification of new SSL/TLS cert registrations.
There could be an increase in financial losses and a surge in cert and domain registrations during the popularity of this tactic. If/when WHOIS goes dark due to GDPR regulations there may also be a surge in domain registrations since it will be easier for phishers to operate with impunity in this environment.
Note: if you are not briefed on what GDPR is or the impact this regulation will have on WHOIS I recommend watching resident expert on GDPR at MarkMonitor Statton Hammock Vice President of Global Policy & Industry Development speak at the recent New York Summit available for viewing here.
As this trend becomes more widespread and awareness grows there will be some distrust of SSL/TLS certs but I view that as a good thing if it encourages more awareness and the realization that consumer data protection really is in the hands of each and every consumer.
BEC scams are still rising
Business email compromise (BEC) scams sometimes called email account compromise (EAC) scams are still increasing because they are generally hard to detect and tend to be successful. Both are generally related to targeted spearphishing attempts to gain data or request an employee process a wire transfer request or change payment routing data in accounts payable.
Often these are executive impersonations having the appearance of a CEO sending an email to the CFO that then asks for a wire transfer to be processed or targeting HR or Payroll employees especially during tax season by asking for a .pdf of each employees’ W-2 tax form. This allows the bad guy to commit tax fraud by filing taxes for refunds in other people’s names. Further yet these scams can be centered around many other things like romance scams lottery employment and home rentals.
According to the Internet Crime Complaint Center IC3 the numbers are jumping! 2017 number will likely be significantly higher when published but in 2015-2016 there was a 2 370% in related losses. In the U.S. there were 22 000 victims and $1.6 billion lost to scams of this nature Oct 2013-Dec 2016. International with domestic: 40 000 victims and $5 billion lost.
The direct impact will be in increased data breaches. The best way for organizations to combat this type of scam is in employee education and awareness plus early indication of likely scammy domain registrations in an effort to block or hopefully re-route any of these emails from going to the intended employee.
There should be checks and balances internally preventing sensitive data from being sent money transferred or account payable data changed without a multi-step multi-person verification process.
Also simply put: there must be an element of skepticism used in email. In Vade Secure’s report on four trends to watch in 2018 they say “with the many data leaks in 2016 and 2017 sophisticated phishing and spear phishing attacks must be expected . . . a simple antispam filter cannot stop a phishing or spear phishing attack.”
Key Takeaways:
- SSL certs can be misused. Losses may increase.
- BEC scams are here to stay; they are too lucrative to go away. Train employees and change internal protocols for processing sensitive data or money transfers and keep an early eye on new domain registrations that are confusingly similar with your own brands